The era of cloud computing has emerged as a game-changer, revolutionizing how organizations operate and innovate. The cloud offers unparalleled agility, scalability, and accessibility, fueling growth and fostering innovation. However, this remarkable transformation also brings forth an array of security challenges that demand our unwavering attention.
As businesses increasingly pivot towards cloud services, entrusting critical functions such as data storage and remote access to this digital realm, the imperative for robust security measures becomes more pronounced than ever before. With each new opportunity the cloud presents, a corresponding security concern arises.
In this comprehensive blog, we embark on an exploration of the complex and dynamic landscape of security in the age of cloud computing. We will navigate through the multifaceted challenges that organizations encounter, dissect effective strategies and best practices to mitigate risks and delve into a real-world example that underscores the paramount importance of adopting a comprehensive security approach.
Evolving Data Security in Cloud Computing
The transition to cloud computing has created a dynamic environment where traditional security models may no longer be sufficient. As data and applications traverse across networks, devices, and cloud providers, securing this digital ecosystem becomes a critical challenge.
Understanding Cloud Security Challenges
- Data Privacy and Compliance: Ensuring compliance with data protection regulations (such as GDPR, HIPAA, etc.) becomes complex when data is stored and processed in various cloud environments.
- Data Breaches and Unauthorized Access: The risk of data breaches and unauthorized access increases as data is transmitted and stored across different networks and servers.
- Shared Responsibility Model: Cloud providers and users share the responsibility of securing the cloud environment, leading to potential gaps in security measures.
- Visibility and Control: Organizations can struggle to maintain visibility and control over their data and applications in the cloud.
Strategies for Ensuring Cloud Security
As organizations harness the power of cloud data security in cloud computing for agility and innovation, they must also fortify their defenses against an evolving spectrum of cyber threats. In this comprehensive guide, we'll delve into strategic measures that not only ensure cloud security but elevate it to an impenetrable fortress.
- Cloud Security Architecture: The foundation of your cloud security strategies begins with crafting a meticulously detailed cloud security architecture. This blueprint should encompass encryption protocols, robust identity and access management frameworks, and meticulous network segmentation. These elements collectively create a resilient barrier against unauthorized access and data breaches.
- Multi-Factor Authentication (MFA): Elevate your security posture by implementing Multi-Factor Authentication (MFA). This additional layer of defense mandates multiple forms of verification, making it exponentially harder for malicious actors to breach your system. MFA is a shield that safeguards critical access points.
- Cloud-Native Security Tools: Cloud service providers offer a suite of cloud-native security tools that are purpose-built to monitor and protect your cloud resources. Leveraging these tools provides real-time insights and proactive threat mitigation, ensuring your cloud environment remains secure and compliant.
- Regular Security Audits: Vigilance is the cornerstone of robust cloud security services. Regularly scheduled security audits and assessments scrutinize your infrastructure for vulnerabilities. Promptly identifying and addressing weaknesses not only bolsters security but also ensures ongoing compliance with industry regulations.
- Securing Patient Data in the Cloud: A Healthcare Success Story A healthcare provider entrusted with safeguarding sensitive patient records in the cloud embarked on a transformative journey to secure cloud data security. Fueled by an unwavering commitment to privacy, they meticulously crafted a holistic cloud security strategy. Encryption became the fortress that shielded patient data, while stringent access controls erected digital barriers.
The relentless pursuit of excellence saw them conducting regular audits, ensuring compliance with stringent healthcare regulations. Through this unwavering dedication, the healthcare provider not only preserved the sanctity of patient information but also set a benchmark for cloud security services in the industry, fostering trust and peace of mind for all stakeholders.
Benefits of Effective Cloud Security
As businesses increasingly rely on the cloud to store, manage, and process their data, it's imperative to understand the profound advantages that robust cloud security brings to the table. Let's explore how this critical shield fortifies organizations on multiple fronts.
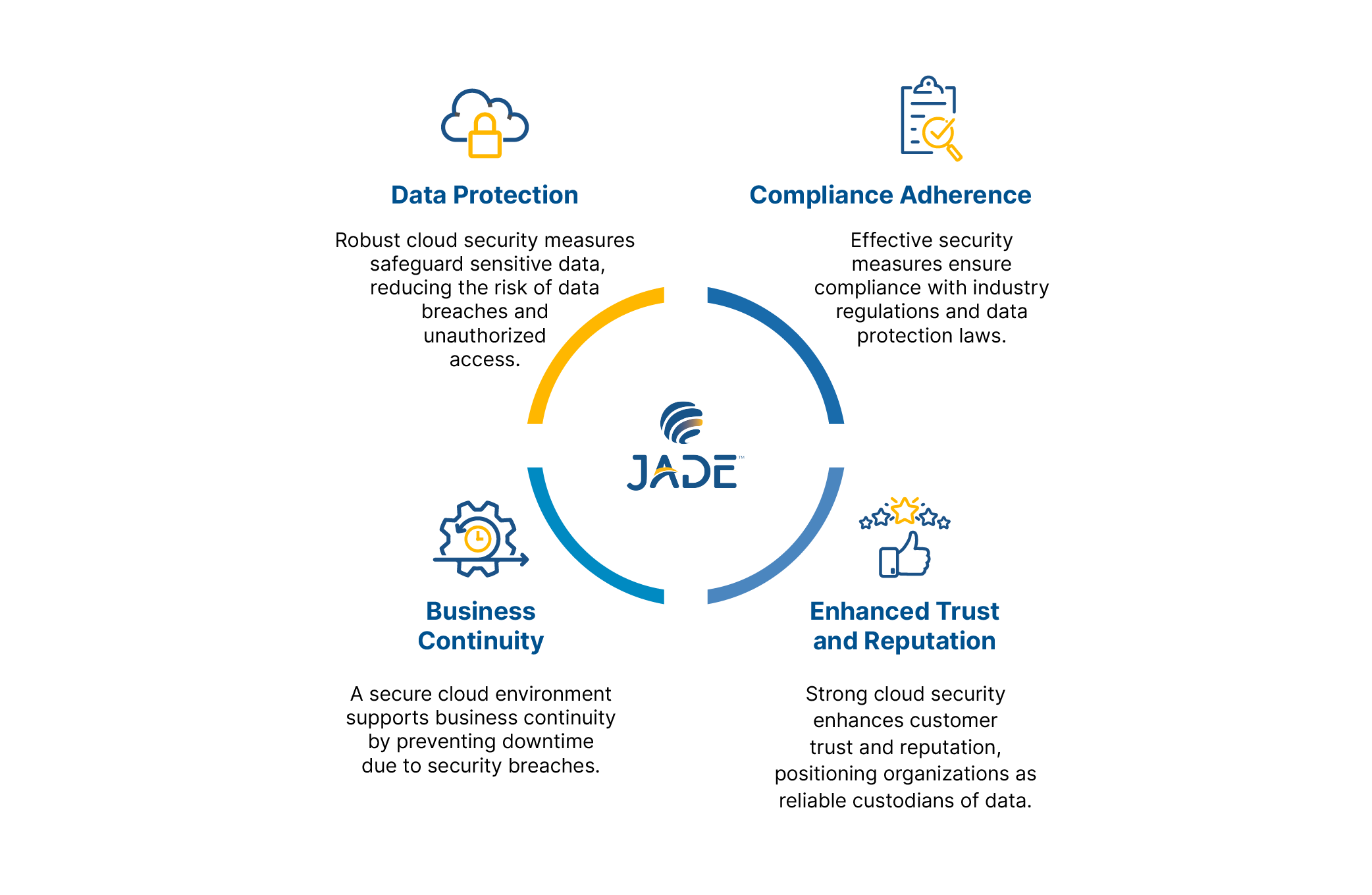
Challenges in Implementing Cloud Security Measures
- Complexity: Managing security across multiple cloud environments and services can be complex and requires careful planning.
- Skills Gap: Organizations may lack the necessary expertise to implement and manage cloud security effectively.
End Note: How is Data Security in Cloud Computing as a Business Imperative
As the cloud continues to shape the digital landscape, ensuring security in the age of cloud has become a business imperative. Organizations must adopt a proactive approach to address the challenges posed by data breaches, compliance, and shared responsibility. By strategizing and implementing robust security measures, businesses can harness the benefits of the cloud while safeguarding their data, applications, and reputation.
The real-world example of a healthcare provider's successful cloud security transformation underscores the tangible impact of effective security strategies. As businesses continue to navigate the complexities of the digital era, a strong commitment to cloud security services will not only protect assets but also empower organizations to innovate, grow, and thrive in the cloud-enabled future.













